WPA uses a Temporal Key Integrity Protocol TKIP and WPA2 uses an Advanced Encryption Standard AES for encryption. Tap Share below the networks name.

Can Someone Explain In Simple Steps How Wpa2 Enterprise Authentication And Encryption Happens Information Security Stack Exchange
Radio range depending on class of radio.

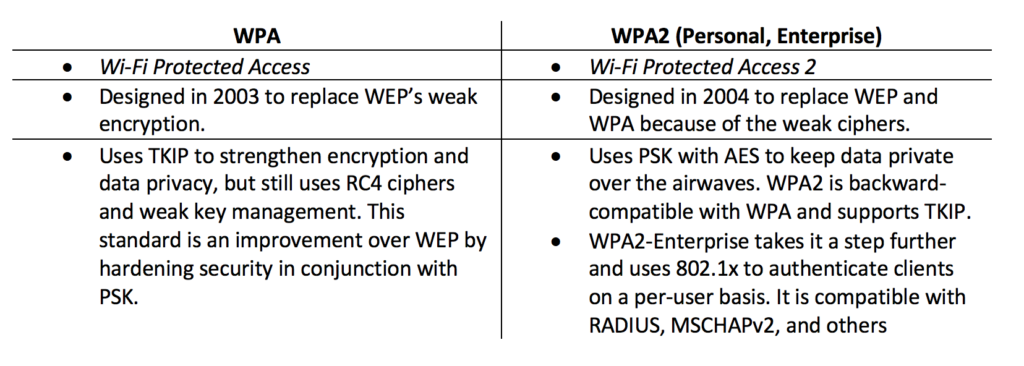
. The user does not understand why the two tools show different IP addresses. - WPA2 is the strongest encryption scheme followed by WPA then WEP. What is the difference between WPA Wi-Fi Protected Access and WPA2 wireless encryption standards.
Instead the private key generator PKG takes its place. Class 1 or 2 or radios. Select Cisco Identity Services Engine ISE Authentication.
Support to NFC pairing for low latency in pairing the BT devices. WPA3-Personal avoids such attacks by strengthening the key exchange between clients and APs through a method knows as SAE Simultaneous Authentication of Equals. The user cannot have cached credentials on the computer the group policy disallows cached credentials.
The central difficulty with asymmetrical encryption methods is the user. Tap the current network or select Saved networks and choose one. This is BEST explained by the interworking of.
WPA2 uses Advanced Encryption. 100 m 10 m or 1 m used in device BT implementation. In this scenario users must be able to communicate with a domain controller on the corporate network for their credentials to.
Two modesdual or single mode devices are used for IoTM2M devices local area network. BT network uses features of self-discovery self-configuration and self-healing. You can select it from a search for wifi via.
This is a central algorithm with which the recipient of an encrypted. In the RADIUS servers field enter the IP address port 1812 and secret of the ISE policy service. Ensure the WPA2-Enterprise radio button is selected along with my RADIUS server in the drop-down menu.
Depending on the context for example an e-mail address or domain could be used. A user checks an IP address using an external website. A user has network-mapped drives that require authentication with the Microsoft Active Directory infrastructure.
First visit the Wi-Fi submenu in your Settings app. WEP is more vulnerable to decryption due to replay. Open the Wi-Fi submenu in Settings.
Personally Identifiable Information PII Which device is likely to use ARM Advanced RISC Machine CPU Central Processing Unit. The address is different than the one the user sees when opening a command prompt and typing in ipconfigall. WPA2 is difficult to crack if protected by a strong password or if deploying enterprise authentication.
This eliminates the need to authenticate public key through official certification bodies. See the plain text password under the QR code. With WPA-Personal and WPA2-Personal modes a malicious user can eavesdrop and capture the four-way handshake between a client and an AP.
Which of the following helps to authenticate the user requesting a password reset over the telephone. Select the SSID from the drop-down menu that is used by the Employee Identity Group. Authenticate yourself if you have device security set up.
Understanding Wi Fi Authentication A Refresher Aruba Blogs

Wpa Wpa2 S5720hi V200r010c00 Configuration Guide Wlan Ac Huawei

Wpa2 Enterprise Secure Your Organization Wi Fi Network

Can Someone Explain In Simple Steps How Wpa2 Enterprise Authentication And Encryption Happens Information Security Stack Exchange
0 Comments